Endep
"Buy endep 25 mg overnight delivery, medicine for depression."
By: Jeanine P. Wiener-Kronish, MD
- Anesthetist-in-Chief, Massachusetts General Hospital, Boston, Massachusetts
The second defect affects performance rather than correctness treatment quadriceps strain endep 25 mg free shipping, and the impact may be inconsequential medications covered by blue cross blue shield buy endep 50mg otc, but the first and third defects can create serious correctness problems treatments yeast infections pregnant 25 mg endep. A file system can provide a different kind of shortcut by maintaining a systemwide sequence number treatment thesaurus purchase 10mg endep overnight delivery, known as a generation number. At some point when the replicas are known to be identical, both file systems record as part of the metadata of every file a start ing generation number, say zero, and they both set their current systemwide generation Saltzer & Kaashoek Ch. Then, whenever a user modifies a file, the file system records in the metadata of that file the current generation number. When the reconciliation program next runs, by examining the generation numbers on each file it can easily determine whether either or both copies of a file were modified since the last reconciliation: if either copy of the file has the current generation number, there is a difference; if both copies of the file have the current generation number, there is a conflict. When the reconciliation is complete and the two replicas are again identical, the file systems both increase their current generation numbers by one in preparation for the next reconciliation. First, they do not allow discovery of decay, since decay events change file contents without updating gen eration numbers. An additional problem that generation numbers do not share with modification timestamps is that implementation of generation numbers is likely to require modifying the file system. The resolution step usually starts with algorithmic handling of as many detected dif ferences as possible, leaving (one hopes) a short list of conflicts for the user to resolve manually. The procedure reconciles two sets of files, named left and right, which were previously reconciled at last reconcile time, which acts as a kind of generation number. The procedure assumes that the two sets of files were identical at that time, and its goal is to make the two sets identical again, by examining the modification timestamps recorded by the storage sys tems that hold the files. The copy operation, in addition to copying a file from one set to another, also copies the time of last modification, if necessary creating a file with the appropriate file name. Line 10 creates an empty list named conflict list, which will accumulate names of any files that it cannot algorithmically reconcile. It starts, on lines 12 and 13, by checking timestamps to see whether either side has modified the file. If both sides have timestamps that are newer than the timestamp of the previous run of the reconciliation program, that indicates that both sides have modified the file, so it adds that file name to the list of conflicts. If only one side has a newer timestamp, it takes the modified ver sion to be the authoritative one and copies it to the other side. Com pletely modularizing these two steps would require two passes through the lists of files, and thereby reduce performance. If they are not, that suggests that the two file systems were different at the end of the previous reconciliation, perhaps because something went wrong during that attempt to reconcile, so the program terminates with an error message rather than blundering for ward and taking a chance on irreparably messing up both file systems. The first case is easily identified by noticing that the side that still has the file has not modified it since the previous run of the reconciliation program. An alternative imple mentation would be to declare a conflict, and ask the user to decide whether to delete or copy the file. Rather than demanding that the user resolve all remaining conflicts on the spot, it would be possible to simply notify the user that there is a non-empty conflict list and let the user resolve those conflicts at leisure. The main complication this improvement adds is that the user is likely to be modifying files (and changing file modification timestamps) at the same time that other file activity is going on, including activity that may be generating new inconsistencies among the replicas. Changes that the user makes to resolve the conflicts may thus look like new conflicts next time the reconciliation program runs. A second complication is that there is no assurance that the user actually reconciles the conflicts; the conflict list may still be non-empty the next time that the reconciliation program runs, and it must take that possibility into account. A simple response could be for the program to start by checking the previous conflict list to see if it is empty, and if it is not asking the user to take care of it before proceeding. Some of the remaining conflicts may actually be algorithmically resolvable, with the help of an application program that understands the semantics and format of a particular file. Consider, for example, an appointment calendar application that stores the entire appointment book in a single file. On the other hand, the calendar application program might be able to resolve the conflict by copying both meeting records to both files. What is needed is for the calendar application to perform the same kind of detection/resolution reconciliation we have already seen, but applied to individual appointment records rather than to the whole file. Of course, if the calendar application encounters two conflicting changes to the same appointment record, it probably would refer that conflict to the user for advice.
A corresponding set of properties must hold for public-key authentication systems: 1 symptoms when quitting smoking buy 75 mg endep mastercard. If the probability is high enough symptoms norovirus 50 mg endep visa, then as a practical matter we can treat such an implementation as being acceptable medications a to z order endep 75mg line. What we require is that the probability of not meeting property 2 be much lower than the likelihood of a human error that leads to treatment interventions buy endep 50 mg a security breach. It is also advisable to change keys periodically to limit the damage in case a key is compromised and crypto graphic protocols often do so (see Section 11. Broadly speaking, the attacks on authentication systems fall in five categories: 1. An adversary may not change the content of M, but just prepend or append some information to the existing content of M. An adversary may have recorded two messages and their tags, and tried to combine them into a new message and tag. Some mathematicians, known as cryptanalysts, are specialists in devising such attacks. To protect messages against the attacks listed above requires a cryptographer who can design the appropriate cryptographic transfor mations on the messages. Thus, we have the worst of two possible worlds: we must achieve a negative goal using complex tools. As a result, even experts have come up with transformations that failed spectacularly. As an example of the importance of keeping track of the window of validity, a team of researchers in 2008 was able to create forged signatures that many Web browsers accepted as valid. Continued research revealed ways of rapidly creating collisions, thus allowing a search for helpful collisions. The connections actually led to impersonation Web sites that were under the control of the research team. If Alice signs the message using public-key cryptography, then Bob verifies the message using a different key from the one that Alice used to com pute the tag. An authentication tag computed with a public-key system is called a digital signature. The digital signature is analogous to a conventional signature because only one person, the holder of the private key, could have applied it. In contrast, the only way to repudiate a digital signature is for Alice to claim that someone else has discovered her private key. Methods for revoking compromised private keys are the subject of considerable debate. Alice and Bob want to sign a contract saying that Alice will Saltzer & Kaashoek Ch. Alice types it up as a document using a word-processing application and both digitally sign it. To his sur prise, Alice presents him with a Word document that states he owes her $100. What Alice did was create a document that included an if statement that changed the displayed content of the document by referring to an external input such as the current date or filename. Thus, even though the signed contents remained the same, the displayed contents changed because they were partially dependent on unsigned inputs. What Bob really knows is that the message originated from a principal that knows key K1. Thus, the way in which keys are bound to principals is an important problem to address. The problem of securely distributing keys is also sometimes called the name-to-key binding problem; in the real world, principals are named by descriptive names rather than keys. So, when we know the name of a principal, we need a method for securely finding the key that goes along with the named principal.
Order endep 10 mg amex. Postpartum Depression ¦ Treatment and Symptoms.
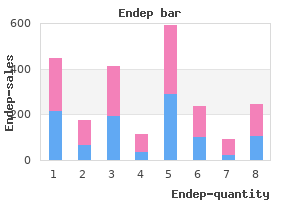
For example symptoms juvenile rheumatoid arthritis buy cheap endep 25mg online, multiple processors are usually asynchronous administering medications 6th edition cheap endep 25mg overnight delivery, and I/O operations are typically performed by an I/O channel processor that is asynchronous with respect to treatment esophageal cancer cheap endep 25mg visa the processor that initiated the I/O symptoms you have cancer buy endep 25mg visa. In a communication network, describes a communication link over which data is sent in frames whose timing relative to other frames is unpredictable and whose lengths may not be uniform. An atomic action can be beforeor-after, which means that its effect is as if it occurred either completely before or completely after any other before-or-after action. An atomic action can also be all-or nothing, which means that if an anticipated failure occurs during the action, the effect of the action as seen by higher layers is either never to have started or else to have completed successfully. An atomic action that is both all-or-nothing and before-or-after is known as a transaction. The bandwidth, the acceptable signal power, and the noise level of a channel together determine the maximum possible data rate for that channel. In digital systems, this term is so often misused as a synonym for maximum data rate that it has now entered the vocabulary of digital designers with that additional meaning. One consequence is that concurrent before-or-after software actions cannot discover the composite nature of one another (that is, one action cannot tell that another has multiple steps). The database literature uses the words "isolation" and "serializable", the operating system literature Saltzer & Kaashoek Ch. Binding may occur at any time up to and including the instant that a name is resolved. The term is also used more generally, meaning to choose a specific lower-layer implementation for some higher-layer feature. Bursts of data are the usual content of messages and the usual payload of packets. When a thread opens a file and performs several write operations, all of the modifications weill be visible to concurrent threads only after the first thread closes the file. In naming, a particular kind of name conflict in which an algorithmic name generator accidentally generates the same name more than once in what is intended to be a unique identifier name space. One usually commits an all-or-nothing action before making its results available to concurrent or later all-or-nothing actions. Before committing, the all-or-nothing action can be abandoned and one can pretend that it had never been undertaken. A committed all-or nothing action cannot be abandoned; if it can be determined precisely how far its results have propagated, it may be possible to reverse some or all of its effects by compensation. Commitment also usually includes an expectation that the results preserve any appropriate invariants and will be durable to the extent that the application requires those properties. Compensation is intrinsically application dependent; it is easier to reverse an incorrect accounting entry than it is to undrill an unwanted hole. Example: a requirement that the balances of all the accounts of a bank sum to zero, or a requirement that a majority of the copies of a set of data be identical. The primary requirement of continuous operation is that it must be possible to perform repair and maintenance without stopping the system. For example, a program with access to a secret might touch several shared but normally unused virtual memory pages in a pattern to bring them into real memory; a conspirator outside the secure area may be able to detect the pattern by measuring the time required to read those same shared pages. The bits may be generated randomly, or they may be a transformed version of a password. The cryptographic key, or at least part of it, usually must be kept secret, while all other components of the transformation can be made public. Such building blocks include functions for implementing encryption and decryption, creating and verifying authentication tags, cryptographic hashes, and pseudorandom number generators. When talking of the data rate of an asynchronous communication link, the term is often used to mean the maximum data rate that the link allows. An error that is not detectable usually leads to a failure, unless some mechanism that is intended to mask some other error accidentally happens to mask the undetectable error. In a discretionary access control system, the owner of an object has the authority to decide which principals have access to that object. It is the abstraction that enforces modularity within a memory, separating modules and allowing for controlled Saltzer & Kaashoek Ch. Compare with stability and persistence, terms that have different technical definitions as explained in Sidebar 2.
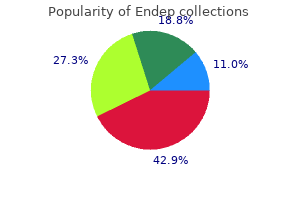
Females with these mutations are hypogonadal and infertile because ovarian follicles do not mature; males exhibit variable degrees of reduced spermatogenesis medications ending in zine 10mg endep with mastercard, presumably because of impaired Sertoli cell function medications japan buy 50mg endep mastercard. Testosterone reaches very high concentrations locally in the testis and is essential for spermatogenesis treatment 99213 quality endep 10mg. Several cytokines and growth factors are also involved in the regulation of spermatogenesis by paracrine and autocrine mechanisms medicine of the people endep 25 mg on line. Testosterone is metabolized predominantly in the liver, although some degradation occurs in peripheral tissues, particularly the prostate and the skin. These compounds undergo glucuronidation or sulfation before being excreted by the kidneys. A polymorphic region in the amino terminus of the receptor, which contains a variable number of glutamine repeats, modifies the transcriptional activity of the receptor. The human Y chromosome contains a small pseudoautosomal region that can recombine with homologous regions of the X chromosome. The physical examination should focus on secondary sex characteristics such as hair growth, gynecomastia, testicular volume, prostate, and height and body proportions. Eunuchoid proportions are defined as an arm span >2 cm greater than height and suggest that androgen deficiency occurred before epiphyseal fusion. Hair growth in the face, axilla, chest, and pubic regions is androgen-dependent; however, changes may not be noticeable unless androgen deficiency is severe and prolonged. Advanced age does not influence testicular size, although the consistency becomes less firm. Asian men generally have smaller testes than western Europeans, independent of differences in body size. Because of its possible role in infertility, the presence of varicocele should be sought by palpation while the patient is standing; it is more common on the left side. In congenital hypogonadotropic hypogonadism, testicular volumes provide a good index for the degree of gonadotropin deficiency and the likelihood of response to therapy. Thus, gonadotropin levels fluctuate, and samples should be pooled or repeated when results are equivocal. Although libido and the overall frequency of sexual acts are decreased in androgen-deficient men, young hypogonadal men may achieve erections in response to visual erotic stimuli. Men with acquired androgen deficiency often report decreased energy and increased irritability. In prepubertal boys, an increase in testosterone to >150 ng/dL indicates the presence of testicular tissue. No response may indicate an absence of testicular tissue or marked impairment of Leydig cell function. Testosterone is generally lower in the late afternoon and is reduced by acute illness. The testosterone concentration in healthy young men ranges from 300 to 1000 ng/dL in most laboratories, although these reference ranges are not derived from population-based random samples. Tracer analogue methods are relatively inexpensive and convenient, but they are inaccurate. Bioavailable testosterone refers to unbound testosterone plus testosterone that is loosely bound to albumin; it can be estimated by the ammonium sulfate precipitation method. Semen volumes and sperm concentrations vary considerably among fertile men, and several samples may be needed before concluding that the results are abnormal. A variety of tests for sperm function can be performed in specialized laboratories, but these add relatively little to the treatment options. Using local anesthesia, fineneedle aspiration biopsy is performed to aspirate tissue for histology. Alternatively, open biopsies can be performed under local or general anesthesia when more tissue is required.
Her medications include diltiazem anima sound medicine purchase endep 10 mg free shipping, cyclosporine medicine used for adhd cheap endep 75mg, prednisone medications grapefruit interacts with cheap 75mg endep, and mycophenolate mofetil treatment 7th feb cheap endep 25 mg online. There is bilateral afferent pupillary defect, and she reports she cannot see out of either eye. A 77-year-old man undergoes coronary artery bypass grafting for refractory angina and three-vessel disease. His physical examination is normal except for poor performance on serial 7 subtraction and only recalling 1 or 3 objects at 15 minutes. During his complicated 3-week course of respiratory failure, he was placed on highfrequency ventilation and prone positioning necessitating paralysis and heavy sedation. While starting his physical therapy, it is noted that he has right footdrop and numbness on the lateral leg. Additional examination reveals a unilateral right motor defect in foot dorsiflexion with intact inversion. There is sensory loss of the lateral aspect of the leg below the knee extending to the dorsum of the foot. A 26-year-old woman presents to the emergency department complaining of shortness of breath and chest pain. These symptoms began abruptly and became progressively worse over 10 minutes, prompting her to call 911. Over this same period, the patient describes feeling her heart pounding and states that she felt like she was dying. It is currently about 20 minutes since the onset of symptoms and the severity has abated, although she continues to feel not back to her baseline. She denies any immediate precipitating cause, although she has been under increased stress as her mother has been hospitalized recently with advanced breast cancer. Her initial vital signs show a heart rate of 108 beats/min, blood pressure 122/68 mmHg, and respiratory rate 20 breaths/min. Reassure the patient and suggest medical and/ or psychological therapy if symptoms recur on a frequent basis. A 36-year-old man is being treated with venlafaxine 150 mg twice daily for major depression. After 2 months, his symptoms were inadequately controlled, necessitating an increase in the dose of venlafaxine from 75 mg twice daily. At that time, he was treated with fluoxetine 80 mg daily for 12 months, but found the sexual side effects difficult to tolerate. He should continue on the medication indefinitely as his depression is likely to recur. The medication can be discontinued safely if he establishes a relationship with a psychotherapist who will monitor his progress and symptoms. The medication can be discontinued safely now as his symptoms are well controlled. The medication should be switched to fluoxetine to complete 12 months of therapy, as this was previously effective for him. Which of the following will lead to a faster rate of absorption of alcohol from the gut into the blood? A 42-year-old woman seeks your advice regarding symptoms concerning for post-traumatic stress disorder. She was the victim of a home invasion 6 months previously where she was robbed and beaten by a man at gunpoint. She thought she was going to die and was hospitalized with multiple blunt force injuries including a broken nose and zygomatic arch. She now states that she is unable to be alone in her home and frequently awakens with dreams of the event. She has worsening insomnia and often stays awake most of the night watching out her window because she is afraid her assailant will return.
Additional information:
References:
- http://www.watsa.org/Resources/Documents/Sexual%20Obsessions%20Article_04.17.15.pdf
- http://www.thebellacademy.com/uploads/2/6/5/6/26569366/all_quiet_on_the_western_front_full_text.pdf
- https://www.scytek.com/InternationalCatalog.pdf